Overview
CYBR is a global leader and pioneer of a new layer of IT security solutions that protects organizations from cyber attacks that have made their way inside the network perimeter to strike at the heart of the enterprise.
Recurring revenue: The renewal rate for each of the years ended December 31, 2011, 2012 and 2013 was over 90%.
52% of revenue is license, 48% is maintenance and professional services.
Reported a loss for the June '14 six months. On an adjusted basis income was down 10% to $2.5 million.
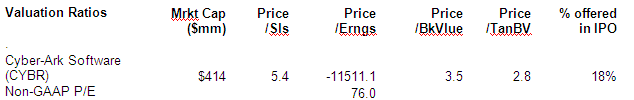
Based in Petach Tikva, Israel, Cyber-Ark Software (CYBR) scheduled a $75 million IPO on NASDAQ with a market capitalization of $414 million at a price range midpoint of $14 for Wednesday, Sept. 24, 2014.
The full IPO calendar is available at IPOpremium. There are nine new IPOs scheduled for the week of September 22.
Manager, Co-managers: J.P. Morgan, Deutsche Bank, Barclays
Joint-managers: William Blair, Nomura Securities, Oppenheimer & Co.
Valuation
Glossary
Conclusion
Positive, 90% of revenue is recurring
Revenue up 33% for the June '14 six months vs the year earlier period
Deferred revenue up 63%
Cash provided by operating activities up 89%
Gross profit of 83%
The loss for the June '14 six months was due primarily to expenses associated with the measurement of fair value of warrants to purchase series B3 preferred shares. But adjusted net income was down -10%.
To put the conclusions and observations in context, the following is reorganized, edited and summarized from the full S-1 referenced above.
Business
CYBR is a global leader and pioneer of a new layer of IT security solutions that protects organizations from cyber attacks that have made their way inside the network perimeter to strike at the heart of the enterprise.
Market growth
According to a 2012 report by International Data Corporation (IDC), worldwide spending on datacenter security solutions was $10.7 billion in 2011 and is expected to grow to $16.5 billion by 2016, representing a compound annual growth rate of 9.3%.
According to the same report, worldwide spending for IT security solutions was $28.4 billion in 2011 and is expected to grow to $40.8 billion in 2016, representing a compound annual growth rate of 7.6%
Software solutions
CYBR’s software solution is focused on protecting privileged accounts, which have become a critical target in the lifecycle of today’s cyber attacks. Privileged accounts are pervasive and act as the “keys to the IT kingdom,” providing complete access to, and control of, all parts of IT infrastructure, industrial control systems and critical business data. In the hands of an external attacker or malicious insider, privileged accounts allow attackers to take control of and disrupt an organization’s IT and industrial control infrastructures, steal confidential information and commit financial fraud.
CYBR’s comprehensive solution proactively protects privileged accounts, monitors privileged activity and detects malicious privileged behavior.
CYBR’s customers use its innovative solution to introduce this new security layer to protect against, detect and respond to cyber attacks before they strike vital systems and compromise sensitive data.
Organizations worldwide are experiencing an unprecedented increase in the sophistication, scale and frequency of cyber attacks.
The challenge this presents is intensified by the growing adoption of new technologies, such as cloud computing, virtualization, software-defined networking, enterprise mobility and social networking, which has resulted in increasingly complex and distributed IT environments with significantly larger attack surfaces.
Organizations have historically relied upon perimeter-based threat protection solutions such as network, web and endpoint security tools as the predominant defense against cyber attacks, yet these traditional solutions have a limited ability to stop today’s advanced threats.
As a result, an estimated 90% of organizations have suffered a cybersecurity breach according to a 2011 survey of approximately 580 U.S. IT practitioners by the Ponemon Institute, a research center focused on privacy, data protection and information security policy.
Organizations are just beginning to adapt their security strategies to address this new threat environment and are evolving their approaches based on the assumption that their network perimeter has been or will be breached.
They are therefore increasingly implementing new layers of security inside the network to disrupt attacks before they result in the theft of confidential information or other serious damage. Regulators are also continuing to mandate rigorous new compliance standards and audit requirements in response to this evolving threat landscape.
CYBR believes that the implementation of a privileged account security solution is one of the most critical layers of an effective security strategy.
Privileged accounts represent one of the most vulnerable aspects of an organization’s IT infrastructure. Privileged accounts are used by system administrators, third-party and cloud service providers, applications and business users, and they exist in nearly every connected device, server, hypervisor, operating system, database, application and industrial control system. Due to the broad access and control they provide, exploiting privileged accounts has become a critical stage of the cyber attack lifecycle.
The typical cyber attack involves an attacker effecting an initial breach, escalating privileges to access target systems, moving laterally through the IT infrastructure to identify valuable targets, and exfiltrating, or stealing, the desired information.
According to Mandiant, credentials of authorized users were hijacked in 100% of the breaches that Mandiant investigated, and privileged accounts were targeted whenever possible.
Intellectual property
As of April 30, 2014, CYBR had two issued patents and ten provisional or pending patent applications in the United States. CYBR also had one patent issued and seven applications pending for examination in non-U.S. jurisdictions, and two pending Patent Cooperation Treaty patent applications, all of which are counterparts of its U.S. patent applications.
The claims for which CYBR has sought patent protection relate to several elements in CYBR’s technology, including the Discovery Engine within its Privileged Account Security Solution, Digital Vault, Privileged Session Manager, Application Identity Manager and Privileged Threat Analytics.
Competition
CYBR believes that none of its competitors offer a fully comprehensive and integrated privileged account security solution; however, CYBR does compete with companies that offer a broad array of IT security products.
CYBR’s current and potential future competitors include CA, Inc., Dell Inc., International Business Machines Corporation and Oracle Corporation, in the access and identity management market, as well as providers of advanced threat protection solutions such as Hewlett-Packard Company, EMC Corporation, International Business Machines Corporation, FireEye, Inc., Splunk Inc. and Palo Alto Networks, Inc. and other smaller companies that offer products with a more limited range of functionality than CYBR’s own offerings.
5% shareholders pre-IPO
Entities affiliated with Jerusalem Venture Partners 46.6%
Entities affiliated with The Goldman Sachs Group, Inc. 24.1%
Entities affiliated with Vertex Venture Capital 11.6%
Cabaret Security Ltd. 7.7%
Dividend Policy
No dividends are planned.
Use of proceeds
CYBR intends to use the $66 million in proceeds from its IPO as follows:
hiring additional sales and marketing and research and development personnel.
CYBR may also use net proceeds from this offering to make acquisitions or investments in complementary companies or technologies, although CYBR does not have any agreement or understanding with respect to any such acquisition or investment at this time.
CYBR does not currently have specific plans or commitments with respect to the net proceeds from this offering and, accordingly, are unable to quantify the allocation of such proceeds among the various potential uses.
