Today's financial markets are more complex than they've ever been, leading many investors to believe their investment strategies have to be equally complicated to work. That's simply not true. In fact, simple is always better… and potentially one whale of a lot more profitable, too.
Today we're going to talk about how a specific event triggered an entry point in an industry that will cost the world's economy $575 billion this year alone. And, as usual, I've got two suggestions for you that could lead to big profits based on a tactic so simple you'll be kicking yourself if you haven't thought about it before.
But first I want to share a story that sets the stage and explains why something America's first millionaire west of the Mississippi did in 1849 is the key to your profits 166 years later. Here's your entry to play the global economy's $575 billion challenge.
Apple (NASDAQ:AAPL) Just Experienced the Unthinkable – and That's Your Opening
Apple has long enjoyed a reputation as a "safer" platform than Windows and Droid by virtue of the fact that its operating systems have been tightly controlled and the applications sold in its App Store are carefully screened. Developers working on even the most minor changes can often wait weeks to hear whether they've been approved or not, for example.
But Apple's veil of impenetrability came crashing down on news that Chinese hackers had planted a malicious program called XcodeGhost in thousands of iOS applications that are used by hundreds of millions of Chinese Apple customers.
The program, like many malicious programs, allows attackers to send commands to infected devices that are then used to steal personal information like names, passwords, financial accounts, and more.
Normally, Apple would catch this kind of stuff when it reviews the coding driving each app. But in this case, the hackers did something very clever. They concocted a counterfeit version of Apple's Xcode toolkit that developers use to create applications and made it available to otherwise legitimate developers, enticing them to use it via faster download speeds.
You wouldn't think something as simple as a faster download would be such a temptation, but in China, it is. That's because the Great Fire Wall of China makes downloading anything from international sites a laborious and tedious process – including legitimate Apple Xcode tools. Domestic Internet speeds are roughly three to five times slower than those in America, to give you an idea.
Anyway, that's why it makes perfect sense that hungry Chinese programmers leapt at the chance to get their hands on domestic Xcode even if it wasn't the real deal, and why the hackers could make their move so easily.
Outside China, the situation is much the same, and the problem is getting worse by the minute. Anybody with a tech device is vulnerable, from the 21 million people exposed when the U.S. Office of Personnel Management got hacked to the 32 million Ashely Madison users who found themselves reeling from lists published to the "dark web."
This kind of stuff is so bad that McAfee Inc. and the Center for Strategic and International Studies estimate that cybercrime will cost the global economy $575 billion this year alone.
According to the Government Accountability Office (GAO), cyberattacks in the United States have increased 1,100% since 2006 – and those are only the incidents the government chooses to acknowledge.
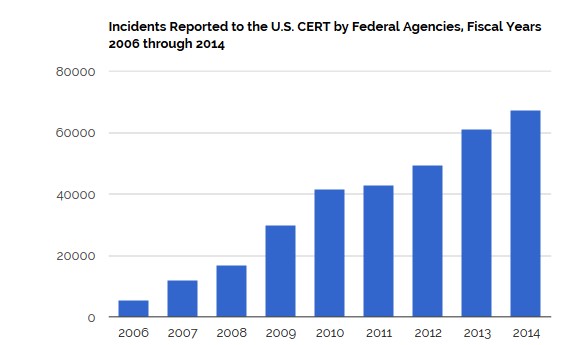
Source: The Government Accountability Office (GAO)
Worldwide, this is a multitrillion-dollar problem. It's also extremely dangerous and goes way beyond apps.
World War III as Einstein Didn't Imagine It
When asked about the frightening development of advanced weapons used in WWII, Albert Einstein reportedly quipped, "I know not what weapons we'll use in World War III, but World War IV will be fought with sticks and stones."
I agree. World War III will be "unlike any other conflict," wrote authors Peter Singer and August Cole in their June 2015 article "The Reality of Cyberwarfare."
When a series of technical glitches halted trading on the New York Stock Exchange last summer, fears immediately turned to a cyberattack, with the term "cyber Pearl Harbor" thrown around. I don't find it particularly reassuring that our government denied a breach, given the state of geopolitics at the moment.
To be very blunt, any investor who has not got this on their radar screen is being naïve. And that brings me back to where we started. Cybersecurity is a complicated field with thousands of players. It'll be hard to sort out the winners because many won't make it.
So you need to take a simple page from history… in 1849.
That's when an estimated 300,000 "forty-niners" took to the hills of California hoping to strike it rich by mining gold. Most didn't, but a man named Samuel Brannan did using a very simple strategy.
He owned the only supply store between San Francisco and the mining fields and became the first millionaire west of the Mississippi by selling picks, shovels, and other essentials to anybody hoping to strike it rich.
I recommend you do the same thing when it comes to cybercrime and data security.
It makes no sense to try and tap into your own gold mine like millions of investors are doing. Instead, I want you to take a page from Brannan's playbook and use another Total Wealth Tactic: Picks & Shovels.
Create Your Own Forty-Niner Fortune
The best way to do that is also the simplest – the PureFunds ISE Cyber Security ETF (NYSE:HACK).
I recently re-recommended it to Money Map Report subscribers because the Apple attack highlighted just how vulnerable everybody is… including those previously thought to be immune from compromise. It's been beaten down 15% since June, which is more than double the corresponding S&P 500 sell-off of only 6.1%.
HACK is made of 32 cybersecurity companies chosen because they're fighting breaches representing 92% of all data breaches. This is stuff like insider misuse, denial of service attacks, point-of-sale theft, and cyber espionage.
The companies included develop a mix of software and hardware while also providing consulting services and/or specific security services directly to their clients.
Each component has to be an operating company and not a closed-end fund or another investment vehicle. So we're talking direct investments here. Moreover, to be included, a company has to have a market capitalization of at least $100 million.
No single component can represent more than 20% of the underlying Cybersecurity Index, so you're not going to have any one security representing a disproportionate amount of risk over time.
Now, I know that some of you reading this will want to play an individual company anyway, so here's one for your consideration – FireEye Inc. (NASDAQ:FEYE). I think the $5.63 billion company is a potential takeover target, and that it'll be Google (NASDAQ:GOOGL) doing the buying.
It's riding high, having beaten Q2 2014 revenue by 56% last quarter, suggesting that the company is pulling ahead of the cybersecurity sector itself. Even more promising to my way of thinking, though, is that the company reported 65% international growth from revenue even as it added 300 more corporate and government clients to its rolls.
That makes sense considering the company's best known product – Mandiant – played a critical role in repairing high-profile cyberattacks at Home Depot (NYSE:HD), Sony (NYSE:SNE), and Anthem (NYSE:ANTM), for example.
In keeping with our preference for deep value and tremendous upside, I love the fact that the company is down 35% from last June following the rumored collapse of buyout talks with Cisco (NASDAQ:CSCO), because that tells me there's plenty of speculative energy powering it.
If there's a drawback, it's that FireEye has a $5.63 billion valuation despite the fact that it has a negative 93.12% profit margin and a negative 38.74% return on equity. Ergo, it's a speculative play of the first order.
So keep any investment to 2% of your capital to limit risk, and make sure you've got a trailing stop in place just in case.
